Creating and managing IAM policies
Crafting and managing IAM policies is an art that requires precision, understanding, and continuous monitoring. As AWS environments evolve, so do the requirements for permissions. In this subsection, we will explore the process of writing IAM policies, delve into advanced conditions, and discuss best practices for testing, versioning, and troubleshooting policies.
Writing IAM policies
IAM policies are structured documents written in JSON format, embodying the principles of the CEDAR policy language, as illustrated in the following diagram (Figure 3.4). Each policy comprises one or more statements, with each statement defining a single permission. A statement encompasses elements such as Effect (allow or deny), Action (the operations you are allowing or denying), Resource (the object the action is performed on), and, when necessary, Condition (the circumstances under which the policy is in effect):
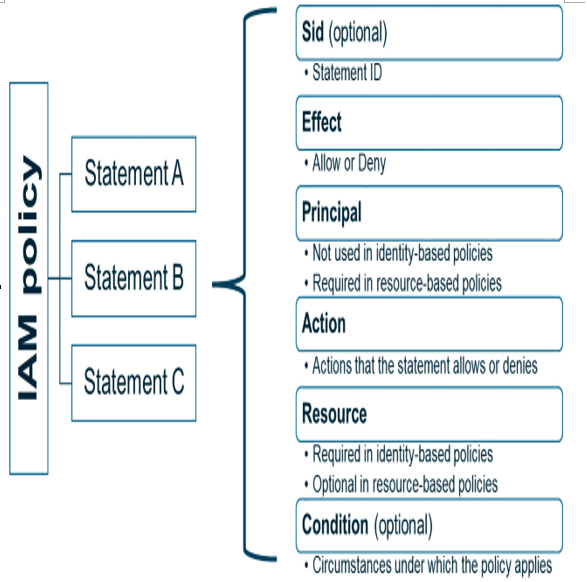
Figure 3.4 – IAM policy structure
It is essential to avoid creating overly permissive policies. Always adhere to the principle of least privilege to ensure that identities only have the permissions they need.
As an example, consider a scenario where you want to grant an IAM identity permission to read objects from a particular S3 bucket. The policy might look something like this:
{
“Version”:
“2012-10-17”,
“Statement”:
[
{
“Effect”:
“Allow”,
“Action”: “s3:GetObject”,
“Resource”: “arn:aws:s3:::example-bucket/*”,
}
]
}
This is a straightforward policy, but as AWS environments grow and requirements change, policies can become more complex.